A personal computer game (also known as a computer game or PC game) is a video game played on a personal computer, rather than on a video game console or arcade machine. Computer games have evolved from the simple graphics and gameplay of early titles like Spacewar!, to a wide range of more visually advanced titles.[1]
PC games are created by one or more game developers, often in conjunction with other specialists (such as game artists) and either published independently or through a third party publisher. They may then be distributed on physical media such as DVDs and CDs, as Internet-downloadable, possibly freely redistributable, software, or through online delivery services such as Direct2Drive and Steam. PC games often require specialized hardware in the user's computer in order to play, such as a specific generation of graphics processing unit or an Internet connection for online play, although these system requirements vary from game to game.
-
History
Although personal computers only became popular with the development of the microprocessor and microcomputer, computer gaming on mainframes and minicomputers had previously already existed. OXO, an adaptation of tic-tac-toe for the EDSAC, debuted in 1952. Another pioneer computer game was developed in 1961, when MIT students Martin Graetz and Alan Kotok, with MIT student Steve Russell, developed Spacewar! on a PDP-1 mainframe computer used for statistical calculations.[2]
The first generation of computer games were often text adventures or interactive fiction, in which the player communicated with the computer by entering commands through a keyboard. An early text-adventure, Adventure, was developed for the PDP-11 minicomputer by Will Crowther in 1976, and expanded by Don Woods in 1977.[3] By the 1980s, personal computers had become powerful enough to run games like Adventure, but by this time, graphics were beginning to become an important factor in games. Later games combined textual commands with basic graphics, as seen in the SSI Gold Box games such as Pool of Radiance, or Bard's Tale for example.
By the late 1970s to early 1980s, games were developed and distributed through hobbyist groups and gaming magazines, such as Creative Computing and later Computer Gaming World. These publications provided game code that could be typed into a computer and played, encouraging readers to submit their own software to competitions.[4] Microchess was one of the first games for microcomputers which was sold to the public. First sold in 1977, Microchess eventually sold over 50,000 copies on cassette tape.
Like with second-generation video game consoles at the time, early home computer games began gaining commercial success by capitalizing on the success of arcade games at the time with ports or clones of popular arcade games.[5][6] By 1982, the top-selling games for the Atari 400 were ports of Frogger and Centipede, while the top-selling game for the Texas Instruments TI-99/4A was the Space Invaders clone TI Invaders.[5] That same year, Pac-Man was ported to the Atari 800,[6] while Donkey Kong was licensed for the Coleco Adam.[7] In late 1981, Atari attempted to take legal action against unauthorized clones, particularly Pac-Man clones, despite some of these predating Atari's exclusive rights to the home versions of Namco's game.[6]
[edit] Industry crash
As the video game market became flooded with poor-quality cartridge games created by numerous companies attempting to enter the market, and over-production of high profile releases such as the Atari 2600 adaptations of Pac-Man and E.T. grossly underperformed, the popularity of personal computers for education rose dramatically. In 1983, consumer interest in console video games dwindled to historical lows, as interest in computer games rose.[8] The effects of the crash were largely limited to the console market, as established companies such as Atari posted record losses over subsequent years. Conversely, the home computer market boomed, as sales of low-cost color computers such as the Commodore 64 rose to record highs and developers such as Electronic Arts benefited from increasing interest in the platform.[8]
The console market experienced a resurgence in the United States with the release of the Nintendo Entertainment System (NES). In Europe, computer gaming continued to boom for many years after.[8] Computers such as the ZX Spectrum and BBC Micro were successful in the European market, where the NES was not as successful despite its monopoly in Japan and North America. The only 8-bit console to have any success in Europe would be the Sega Master System.[9] Meanwhile in Japan, both consoles and computers became major industries, with the console market dominated by Nintendo and the computer market dominated by NEC's PC-88 (1981) and PC-98 (1982). A key difference between Western and Japanese computers at the time was the display resolution, with Japanese systems using a higher resolution of 640x400 to accommodate Japanese text which in turn had an impact on game design and allowed more detailed graphics.[10]
[edit] New genres
Increasing adoption of the computer mouse, driven partially by the success of games such as the highly successful King's Quest series, and high resolution bitmap displays allowed the industry to include increasingly high-quality graphical interfaces in new releases. Meanwhile, the Commodore Amiga computer achieved great success in the market from its release in 1985, contributing to the rapid adoption of these new interface technologies.[11]
Further improvements to game artwork were made possible with the introduction of FM synthesis sound. Yamaha began manufacturing FM synth boards for computers in the early-mid 1980s, and by 1985, the FM-7 AV computer had built-in FM sound.[10] The first sound cards, such as AdLib's Music Synthesizer Card, soon appeared in 1987. These cards allowed IBM PC compatible computers to produce complex sounds using FM synthesis, where they had previously been limited to simple tones and beeps. However, the rise of the Creative Labs Sound Blaster card, released in 1989, which featured much higher sound quality due to the inclusion of a PCM channel and digital signal processor, led AdLib to file for bankruptcy by 1992. Also in 1989, the FM Towns computer included built-in PCM sound, in addition to a CD-ROM drive and 24-bit color graphics.[10]
In 1991, id Software produced an early first-person shooter, Hovertank 3D, which was the company's first in their line of highly influential games in the genre. There were also several other companies that produced early first-person shooters, such as Arsys Software's Star Cruiser,[12] which featured fully 3D polygonal graphics in 1988,[13] and Accolade's Day of the Viper in 1989. Id Software went on to develop Wolfenstein 3D in 1992, which helped to popularize the genre, kick-starting a genre that would become one of the highest-selling in modern times.[14] The game was originally distributed through the shareware distribution model, allowing players to try a limited part of the game for free but requiring payment to play the rest, and represented one of the first uses of texture mapping graphics in a popular game, along with Ultima Underworld.[15]
While leading Sega and Nintendo console systems kept their CPU speed at 3-7 MHz, the 486 PC processor ran much faster, allowing it to perform many more calculations per second. The 1993 release of Doom on the PC was a breakthrough in 3D graphics, and was soon ported to various game consoles in a general shift toward greater realism.[16] In the same time frame, games such as Myst took advantage of the new CD-ROM delivery format to include many more assets (sound, images, video) for a richer game experience.
Many early PC games included extras such as the peril-sensitive sunglasses that shipped with The Hitchhiker's Guide to the Galaxy. These extras gradually became less common, but many games were still sold in the traditional over-sized boxes that used to hold the extra "feelies". Today, such extras are usually found only in Special Edition versions of games, such as Battlechests from Blizzard.[17]
[edit] Contemporary gaming
By 1996, the rise of Microsoft Windows and success of 3D console titles such as Super Mario 64 sparked great interest in hardware accelerated 3D graphics on the IBM PC compatible, and soon resulted in attempts to produce affordable solutions with the ATI Rage, Matrox Mystique and S3 ViRGE. Tomb Raider, which was released in 1996, was one of the first third person shooter games and was praised for its revolutionary graphics. As 3D graphics libraries such as DirectX and OpenGL matured and knocked proprietary interfaces out of the market, these platforms gained greater acceptance in the market, particularly with their demonstrated benefits in games such as Unreal.[18] However, major changes to the Microsoft Windows operating system, by then the market leader, made many older MS-DOS-based games unplayable on Windows NT, and later, Windows XP (without using an emulator, such as DOSbox).[19][20]
The faster graphics accelerators and improving CPU technology resulted in increasing levels of realism in computer games. During this time, the improvements introduced with products such as ATI's Radeon R300 and NVidia's GeForce 6 Series have allowed developers to increase the complexity of modern game engines. PC gaming currently tends strongly toward improvements in 3D graphics.[21]
Unlike the generally accepted push for improved graphical performance, the use of physics engines in computer games has become a matter of debate since announcement and 2005 release of the nVidia PhysX PPU, ostensibly competing with middleware such as the Havok physics engine. Issues such as difficulty in ensuring consistent experiences for all players,[22] and the uncertain benefit of first generation PhysX cards in games such as Tom Clancy's Ghost Recon Advanced Warfighter and City of Villains, prompted arguments over the value of such technology.[23][24]
Similarly, many game publishers began to experiment with new forms of marketing. Chief among these alternative strategies is episodic gaming, an adaptation of the older concept of expansion packs, in which game content is provided in smaller quantities but for a proportionally lower price. Titles such as Half-Life 2: Episode One took advantage of the idea, with mixed results rising from concerns for the amount of content provided for the price.[25]
[edit] PC game development
Game development, as with console games, is generally undertaken by one or more game developers using either standardized or proprietary tools. While games could previously be developed by very small groups of people, as in the early example of Wolfenstein 3D, many popular computer games today require large development teams and budgets running into the millions of dollars.[26]
PC games are usually built around a central piece of software, known as a game engine,[27] that simplifies the development process and enables developers to easily port their projects between platforms. Unlike most consoles, which generally only run major engines such as Unreal Engine 3 and RenderWare due to restrictions on homebrew software, personal computers may run games developed using a larger range of software. As such, a number of alternatives to expensive engines have become available, including open source solutions such as Crystal Space, OGRE and DarkPlaces.
[edit] User-created modifications
The multi-purpose nature of personal computers often allows users to modify the content of installed games with relative ease. Since console games are generally difficult to modify without a proprietary software development kit, and are often protected by legal and physical barriers against tampering and homebrew software,[28][29] it is generally easier to modify the personal computer version of games using common, easy-to-obtain software. Users can then distribute their customised version of the game (commonly known as a mod) by any means they choose.
The inclusion of map editors such as UnrealEd with the retail versions of many games, and others that have been made available online such as GtkRadiant, allow users to create modifications for games easily, using tools that are maintained by the games' original developers. In addition, companies such as id Software have released the source code to older game engines, enabling the creation of entirely new games and major changes to existing ones.[30]
Modding had allowed much of the community to produce game elements that would not normally be provided by the developer of the game, expanding or modifying normal gameplay to varying degrees. Arguably, the most notable example is Counter-Strike, a mod for Half Life. Counter-Strike turned the initial adventure FPS into a round based, tactical FPS.
[edit] Distribution
[edit] Physical distribution
Computer games are typically sold on standard storage media, such as compact discs, DVD, and floppy disks.[31] These were originally passed on to customers through mail order services,[32] although retail distribution has replaced it as the main distribution channel for video games due to higher sales.[33] Cassette tapes[34] and different formats of floppy disks were initially the staple storage media of the 1980s and early 1990s, but have fallen out of practical use as the increasing sophistication of computer games raised the overall size of the game's data and program files.
The introduction of complex graphics engines in recent times has resulted in additional storage requirements for modern games, and thus an increasing interest in CDs and DVDs as the next compact storage media for personal computer games. The rising popularity of DVD drives in modern PCs, and the larger capacity of the new media (a single-layer DVD can hold up to 4.7 gigabytes of data, more than five times as much as a single CD), have resulted in their adoption as a format for computer game distribution. To date, CD versions are still offered for most games, while some games offer both the CD and the DVD versions.
[edit] Shareware
Main articles: Shareware and Game demo
Shareware marketing, whereby a limited or demonstration version of the full game is released to prospective buyers without charge, has been used as a method of distributing computer games since the early years of the gaming industry and was seen in the early days of Tanarus as well as many others. Shareware games generally offer only a small part of the gameplay offered in the retail product, and may be distributed with gaming magazines, in retail stores or on developers' websites free of charge.
In the early 1990s, shareware distribution was common among fledging game companies such as Apogee Software, Epic Megagames and id Software, and remains a popular distribution method among smaller game developers. However, shareware has largely fallen out of favor among established game companies in favour of traditional retail marketing, with notable exceptions such as Big Fish Games and PopCap Games continuing to use the model today.[35]
[edit] Online delivery
With the increased popularity of the Internet, online distribution of game content has become more common.[36] Retail services such as Direct2Drive and Download.com allow users to purchase and download large games that would otherwise only be distributed on physical media, such as DVDs, as well as providing cheap distribution of shareware and demonstration games. Companies such as Real Networks provide a service that allows other websites to use their game catalog and ecommerce backend to publish their own game download distribution sites. Other services, allow a subscription-based distribution model in which users pay a monthly fee to download and play as many games as they wish.
The Steam system, developed by Valve Corporation, provides an alternative to traditional online services. Instead of allowing the player to download a game and play it immediately, games are made available for "pre-load" in an encrypted form days or weeks before their actual release date. On the official release date, a relatively small component is made available to unlock the game. Steam also ensures that once bought, a game remains accessible to a customer indefinitely, while traditional mediums such as floppy disks and CD-ROMs are susceptible to unrecoverable damage and misplacement. The user would however depend on the Steam servers to be online to download its games. According to the terms of service for Steam, Valve has no obligation to keep the servers running. Therefore, if the Valve Corporation shut down, so would the servers. However, they have stated that if the service was to be discontinued, games would no longer require authorization from the servers to run. Nevertheless, they are not obligated to do so.
[edit] PC game genres
The real-time strategy genre, which accounts for more than a quarter of all PC games sold,[1] has found very little success on video game consoles, with releases such as Starcraft 64 failing in the marketplace. Real-time strategy games tend to suffer from the design of console controllers, which do not allow fast, accurate movement.[37]
[edit] PC gaming technology
[edit] Hardware
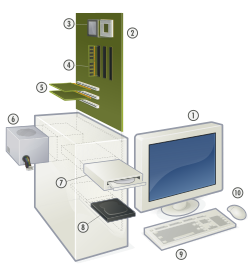
Modern computer games place great demand on the computer's hardware, often requiring a fast central processing unit (CPU) to function properly. CPU manufacturers historically relied mainly on increasing clock rates to improve the performance of their processors, but had begun to move steadily towards multi-core CPUs by 2005. These processors allow the computer to simultaneously process multiple tasks, called threads, allowing the use of more complex graphics, artificial intelligence and in-game physics.[21][38]
Similarly, 3D games often rely on a powerful graphics processing unit (GPU), which accelerates the process of drawing complex scenes in realtime. GPUs may be an integrated part of the computer's motherboard, the most common solution in laptops,[39] or come packaged with a discrete graphics card with a supply of dedicated Video RAM, connected to the motherboard through either an AGP or PCI-Express port. It is also possible to use multiple GPUs in a single computer, using technologies such as NVidia's Scalable Link Interface and ATI's CrossFire.
Sound cards are also available to provide improved audio in computer games. These cards provide improved 3D audio and provide audio enhancement that is generally not available with integrated alternatives, at the cost of marginally lower overall performance.[40] The Creative Labs SoundBlaster line was for many years the de facto standard for sound cards, although its popularity dwindled as PC audio became a commodity on modern motherboards.
Physics processing units (PPUs), such as the Nvidia PhysX (formerly AGEIA PhysX) card, are also available to accelerate physics simulations in modern computer games. PPUs allow the computer to process more complex interactions among objects than is achievable using only the CPU, potentially allowing players a much greater degree of control over the world in games designed to use the card.[39]
Virtually all personal computers use a keyboard and mouse for user input. Other common gaming peripherals are a headset for faster communication in online games, joysticks for flight simulators, steering wheels for driving games and gamepads for console-style games.
[edit] Software
Computer games also rely on third-party software such as an operating system (OS), device drivers, libraries and more to run. Today, the vast majority of computer games are designed to run on the Microsoft Windows family of operating systems. Whereas earlier games written for MS-DOS would include code to communicate directly with hardware, today Application programming interfaces (APIs) provide an interface between the game and the OS, simplifying game design. Microsoft's DirectX is an API that is widely used by today's computer games to communicate with sound and graphics hardware. OpenGL is a cross-platform API for graphics rendering that is also used. The version of the graphics card's driver installed can often affect game performance and gameplay. It is not unusual for a game company to use a third-party game engine, or third-party libraries for a game's AI or physics.
[edit] Multiplayer
[edit] Local area network gaming
Multiplayer gaming was largely limited to local area networks (LANs) before cost-effective broadband Internet access became available, due to their typically higher bandwidth and lower latency than the dial-up services of the time. These advantages allowed more players to join any given computer game, but have persisted today because of the higher latency of most Internet connections and the costs associated with broadband Internet.
LAN gaming typically requires two or more personal computers, a router and sufficient networking cables to connect every computer on the network. Additionally, each computer must have a network card in order to communicate with other computers on the network, and its own copy (or spawn copy) of the game in order to play. Optionally, any LAN may include an external connection to the Internet.
[edit] Online games
Main article: Online game
Online multiplayer games have achieved popularity largely as a result of increasing broadband adoption among consumers. Affordable high-bandwidth Internet connections allow large numbers of players to play together, and thus have found particular use in massively multiplayer online role-playing games, Tanarus and persistent online games such as World War II Online.
Although it is possible to participate in online computer games using dial-up modems, broadband internet connections are generally considered necessary in order to reduce the latency between players (commonly known as "lag"). Such connections require a broadband-compatible modem connected to the personal computer through a network interface card (generally integrated onto the computer's motherboard), optionally separated by a router. Online games require a virtual environment, generally called a "game server". These virtual servers inter-connect gamers, allowing real time, and often fast paced action. To meet this subsequent need, Game Server Providers (GSP) have become increasingly more popular over the last half decade. While not required for all gamers, these servers provide a unique "home", fully customizable (such as additional modifications, settings, etc.) - giving the end gamers the experience they desire. Today there are over 510,000 game servers hosted in North America alone.[41]
[edit] Emulation
Emulation software, used to run software without the original hardware, are popular for their ability to play legacy video games without the consoles or operating system for which they were designed. The operating system emulators include DOSBox, a DOS emulator which allows playing games developed originally for this operating system and thus not compatible with a modern day OS. Console emulators such as NESticle and MAME are relatively commonplace, although the complexity of modern consoles such as the Xbox or PlayStation makes them far more difficult to emulate, even for the original manufacturers.[42]
Most emulation software mimics a particular hardware architecture, often to an extremely high degree of accuracy. This is particularly the case with classic home computers such as the Commodore 64, whose software often depends on highly sophisticated low-level programming tricks invented by game programmers and the demoscene.
[edit] Controversy
PC games have long been a source of controversy, particularly related to the violence that has become commonly associated with video gaming in general. The debate surrounds the influence of objectionable content on the social development of minors, with organisations such as the American Psychological Association concluding that video game violence increases children's aggression,[43] a concern that prompted a further investigation by the Center for Disease Control in September 2006.[44] Industry groups have responded by noting the responsibility of parents in governing their children's activities, while attempts in the United States to control the sale of objectionable games have generally been found unconstitutional.[45]
Video game addiction is another cultural aspect of gaming to draw criticism as it can have a negative influence on health and on social relations. The problem of addiction and its health risks seems to have grown with the rise of Massively Multiplayer Online Role Playing Games (MMORPGs).[46] Alongside the social and health problems associated with computer game addiction have grown similar worries about the effect of computer games on education.[47]
[edit] Computer games museums
There are several computer games museums around the world. In 2011 one opened in Berlin, a computer game museum that documents computer games from the 1970s until today.
-